Background
In this post I'll be walking though CVE-2023-29301, which is an access control bypass / password brute force vulnerability in Adobe ColdFusion that I reported to Adobe and was fixed on July 11, 2023 in Adobe Product Security Bulletin APSB23-40. Note that this is an access control bypass and is not an authentication bypass vulnerability.
Vulnerability Summary
Technical Details
The ColdFusion Administrator (CFAdmin) is the central interface to configure and manage your ColdFusion servers. Admin users can authenticate via username/password (and via LDAP, as of ColdFusion 2023), and are then able to view and configure many settings.
Restricting access to CFAdmin is highly recommended as one step toward preventing unauthorized access and decreasing overall attack surface. Within CFAdmin, you can configure the IP addresses that are permitted to access CFAdmin, in Security → Allowed IP Addresses. (And beyond these native IP address restrictions, it is advisable to have additional layers of access control, such as WAF rules, URL filtering, and web server access control rules protecting CFAdmin.)
These IP address restrictions are enforced by the coldfusion.filter.IPFilterUtils class, which controls access to various paths that contain administrative components and other sensitive functionality:
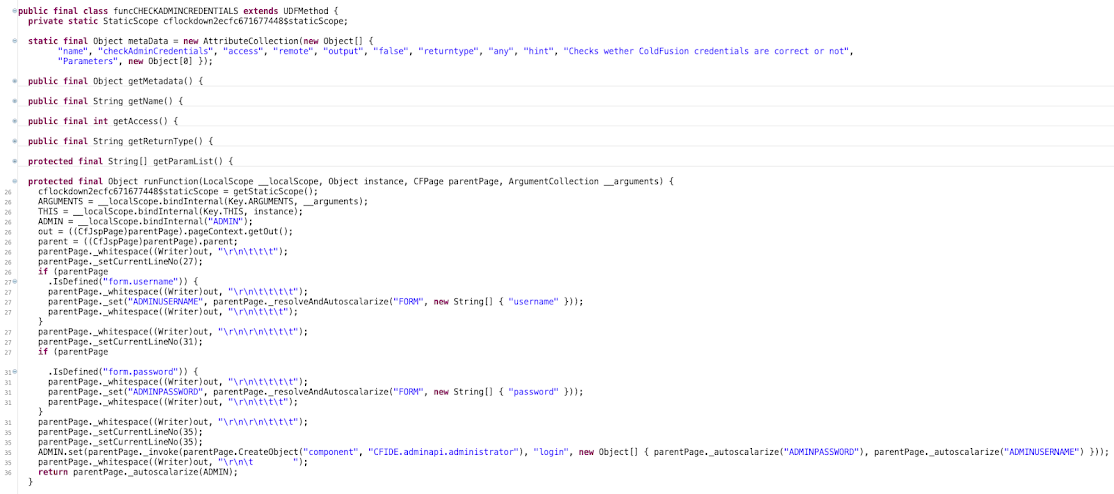
An unpatched version of coldfusion.filter.IPFilterUtils.class is shown above. The vulnerability stems from the fact that an attacker is able to interact with a CFAdmin component, lockdown.cfc, whose path is absent from the list above. As you can see, IPFilterUtils does not restrict access to /CFIDE/lockdown paths. The file /CFIDE/lockdown/lockdown.cfc is is an already-compiled Java class (it is not plaintext CFML source code that is compiled at runtime), and contains a remote CFC method named checkAdminCredentials:
By passing adminUsername and adminPassword request parameters (or username and password POST parameters) to this method, it's possible to make requests and determine valid CFAdmin credentials. The request/response below shows a successful authentication attempt for username groucho and password swordfish.
Request:
Host: some-coldfusion-target
Content-Type: application/x-www-form-urlencoded
Content-Length: 34
username=groucho&password=swordfish
Response:
<wddxPacket version='1.0'><header/><data><boolean value='true'/></data></wddxPacket>
In the case of invalid username/password values, the boolean value in the WDDX packet will be 'false'.
This vulnerability can be used to brute-force a valid admin password from an untrusted IP address. Additionally, lockdown.cfc could also be used as a means to reach vulnerable codepaths that rely on ColdFusion Components (CFC) and remote methods, such as CVE-2023-26360 and CVE-2023-38203.
This is an access control bypass and is not an authentication bypass vulnerability. Furthermore, only the authentication endpoint can be access via this bypass technique, and not the entire ColdFusion Administrator web interface. Adobe assessed this with a CVSS score of 5.9 and a rating of "Important," which I agree is appropriate. While it is not as critical and impactful as some other recent ColdFusion vulnerabilities, it has the potential to be combined with other vulnerabilities and techniques, to be used as a handy link an an attacker's larger exploit chain.
Remediation Recommendations
- Upgrade ColdFusion to a version that is not affected by this vulnerability, and follow the other Solutions in APSB23-40
- Ensure that CFAdmin components are protected with multiple layers of security, such as WAF rules, URL filtering, and web server access control rules
- If possible, consider blocking all remote HTTP access to .cfc files
Timeline
2023-05-20 - Reported the vulnerability to Adobe PSIRT
2023-07-11 - Adobe releases APSB23-40, which includes patches for this vulnerability
2023-08-30 - Blog post published.


No comments:
Post a Comment